Troubleshooting Tip
I was asked to help with a webserver whose web pages could not be browsed/accessed from outside.
The first thing i did was to check for network connectivity. If i could ping the server and it responded, then it means there is a valid network connection between the web server and my PC.
c:\>ping 202.91.xxx.xx5
Pinging 202.91.xxx.xx5 with 32 bytes of data:
Reply from 202.91.xxx.xx5: bytes=32 time=44ms TTL=120
Reply from 202.91.xxx.xx5: bytes=32 time=46ms TTL=120
Reply from 202.91.xxx.xx5: bytes=32 time=49ms TTL=120
Reply from 202.91.xxx.xx5: bytes=32 time=46ms TTL=120
The next step was to see if I could browse the site from INSIDE the web server. If i could not browse from INSIDE the webserver, then it means that there was an error in provisioning the website in IIS. For this test, i simply fired up the Internet explorer and entered the UR L (Uniform resource locator). The URL format is something like this: http://www.google.com
If you dont see any error messages, but instead, see the website pop up, then the next logical step would be to take a look at the firewall settings of your windows web server.
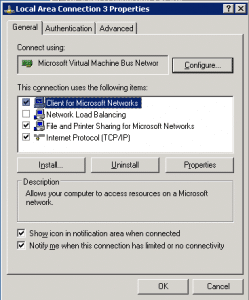
On a Windows 2003 or older machine, you go to the /control panel/network connections and select the network card. On the next popup window, click on Properties
You will then see the Local Area Connections Properties. Click [Advance] to show the Windows Firewall settings.
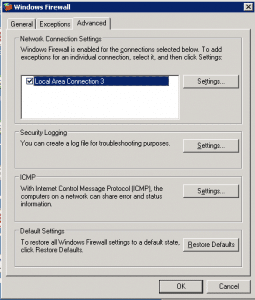
Click [Advance] a second time to show the Network Connections Settings:
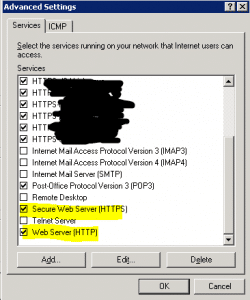
From here, click on [Settings] to show the configurable options:
Make sure that the items highlighted in yellow are CLICKED (enabled).
No Comments »
Filed under: Computing, Security, SEO